Module 2: Social Engineering and Malware Threats
Introduction
Cyber threats are not always technical; sometimes, they rely on human error. Social engineering and malware are two common tactics used by cybercriminals to exploit vulnerabilities.
Page 1: Understanding Social Engineering
Before diving into specific tactics, it is important to understand that social engineering manipulates human psychology rather than relying on technical hacks. Attackers exploit trust, curiosity, or fear to deceive people into surrendering sensitive information or compromising security systems.
Recognizing these tactics can empower you to defend against them.
- Phishing emails: Fraudulent messages that appear legitimate, often mimicking trusted organizations to trick you into revealing personal information or clicking malicious links.
- Pretexting: Attackers create a fabricated scenario to obtain sensitive information. For example, pretending to be tech support asking for your login details.
- Baiting: Offering something enticing, such as free software or media downloads, which leads to malware infection or personal data theft.
- Tailgating: Physically following authorized personnel into restricted areas without proper credentials, thereby gaining access to sensitive environments.
Example of a Phishing SMS:
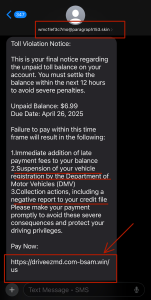
Page 2: Defense Strategies
To effectively guard against social engineering attacks, it is essential to practice vigilance and adopt a mindset of healthy skepticism. Cybercriminals depend on hurried decisions and unexamined trust. Developing a habit of careful scrutiny can disrupt their tactics.
- Scrutinize unsolicited emails and verify the sender. Check for subtle errors in email addresses or domains that could indicate a scam.
- Avoid clicking suspicious links or downloading unverified attachments, which may contain hidden malware.
- Enable MFA for added protection, providing a safety net even if your credentials are compromised.
- Limit personal information shared online, as oversharing can make you a target for social engineering tactics.
Page 3: Understanding Malware
Malware is a broad term for malicious software designed to infiltrate or damage your devices and data. Cybercriminals use various tactics to distribute malware, often hiding it in legitimate-looking content or exploiting outdated systems. By understanding how malware spreads, you can take preventive action to safeguard your technology and personal information.
- Phishing emails: Clicking malicious links or downloading infected attachments initiates malware infections.
- Drive-by downloads: Visiting compromised websites may automatically trigger malware downloads without your consent.
- Infected USB devices: Malware can spread when you insert a compromised external drive into your computer.
- Outdated software: Cybercriminals exploit vulnerabilities in outdated software to deploy malware.
Page 4: Warning Signs of Malware Infection
Malware often operates silently, but there are warning signs that can alert you to its presence. Recognizing these symptoms early allows you to respond swiftly, minimizing potential damage and protecting your data.
- Sluggish system performance: Hidden malware processes consume resources, causing your device to slow down unexpectedly.
- Unexpected pop-ups: Frequent, random advertisements or alerts can be a sign of malicious software.
- Unauthorized system changes: Altered browser settings or unfamiliar programs indicate possible malware activity.
- Loss or corruption of files: Missing or unusable files may result from ransomware or other destructive malware.
Reflection: Have you ever received a suspicious email or encountered unexpected system behavior? How did you respond?
Media Attributions
- Phishing SMS example © Luis Mayorga Soza
