Module 1: Protecting Yourself Online – Cybersecurity Essentials
Introduction
Imagine logging into your college email and finding that your account has been compromised. Sensitive information is now exposed, and your personal data is at risk. How could this have been prevented?
Cybersecurity refers to the measures and protocols designed to protect data, devices, and networks from unauthorized access or attacks. As digital citizens, it is our responsibility to understand these tools and use them effectively.
Page 1: Key Concepts in Cybersecurity
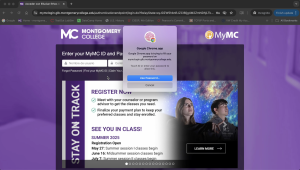
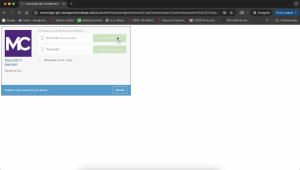
Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA)
- 2FA requires two forms of verification, typically a password and a code sent to your phone. This means that even if a hacker discovers your password, they still need your secondary verification method, providing an additional barrier against unauthorized access.
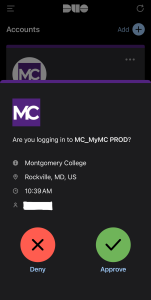
- MFA extends this by including a third factor, such as a fingerprint or facial recognition. These biometric verifications are extremely difficult for attackers to replicate, enhancing your account security.
How Multi-Factor Authentication works within Montgomery College:
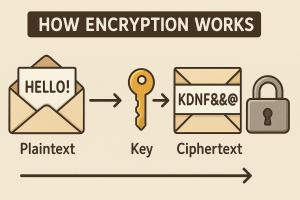
Encryption
- Encryption converts data into coded formats that are unreadable without the proper key. This ensures that even if data is intercepted, it remains inaccessible to unauthorized users.
- Protocols like SSL (Secure Sockets Layer) and TLS (Transport Layer Security) secure data transmission between your device and websites, protecting sensitive information like passwords and credit card numbers during online transactions.
Firewalls and Antivirus Software
- Firewalls monitor and control network traffic, blocking suspicious activity before it can reach your system. They act as a shield between your computer and potential cyber threats.
- Antivirus software scans for and removes malicious software, keeping your devices secure from malware, ransomware, and spyware attacks.
Reflection: Consider the tools you currently use to protect your online accounts. Are they sufficient? What additional measures could you implement?
Activity 1: Create a checklist of cybersecurity tools you currently use. Identify at least two new measures you can adopt this week to strengthen your online safety.
Media Attributions
- Multi-Factor Authentication in MC’s website 1 © Luis Mayorga Soza
- Multi-Factor Authentication in MC’s website 2 © Luis Mayorga Soza
- Multi-Factor Authentication in MC’s website 3 © Luis Mayorga Soza
- Encrption ChatGPT Image May 7, 2025, 10_30_32 AM © ChatGPT, Luis Mayorga Soza
